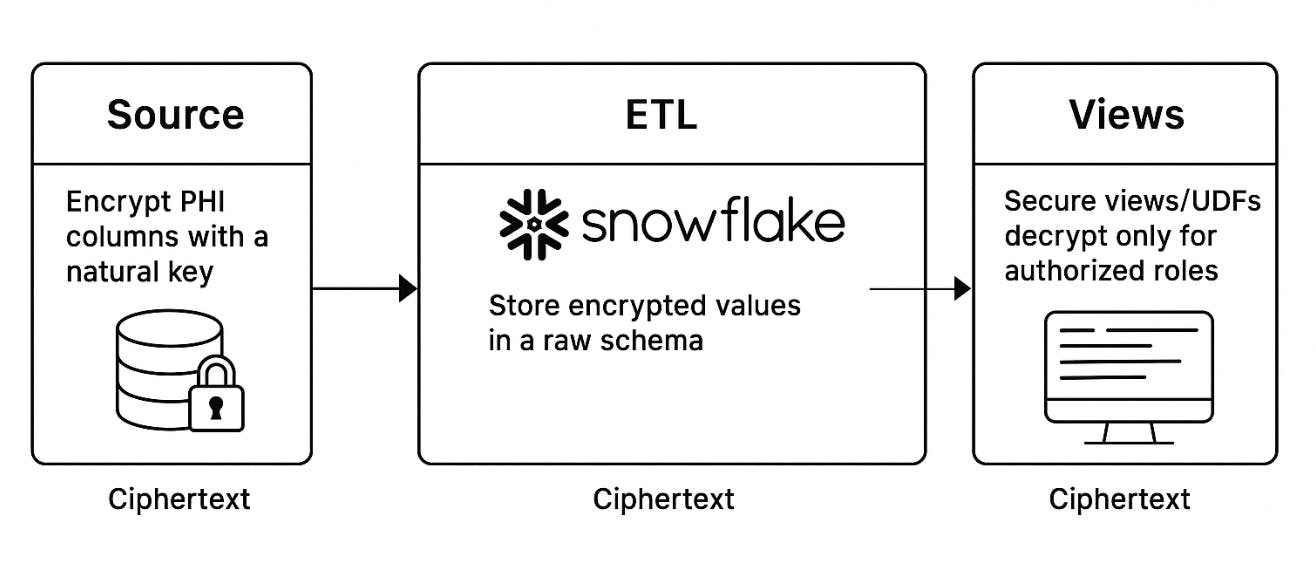
Protecting sensitive healthcare data while embracing artificial intelligence can be achieved through end-to-end encryption in ETL pipelines. By encrypting PHI at the source, maintaining that encryption in Snowflake, and decrypting only for approved roles, organizations meet HIPAA standards and still unlock the power of secure ML and generative AI.
How I Secured PHI in ETL Pipelines While Powering AI in Snowflake
Key Takeaways:
- PHI data should be encrypted at the source before ETL.
- End-to-end encryption supports HIPAA compliance.
- Decryption should occur strictly on-demand for authorized personnel.
- Preventing insider leaks is as vital as shielding against external threats.
- Robust encryption practices enable cutting-edge AI in Snowflake ML and Cortex.
The Need for Comprehensive PHI Security in ETL
Protecting protected health information (PHI) is a top priority for any organization handling healthcare data. “Encrypt PHI data at the source” is the foundational advice that sets the stage for robust security. Strict regulations, such as HIPAA, demand that confidentiality remains intact from the point of data creation onward, ensuring patient privacy and legal compliance.
End-to-End Encryption Through the Pipeline
One key to success lies in maintaining encryption as data moves through every stage of the ETL pipeline. This approach prevents unauthorized exposure and helps organizations remain HIPAA-compliant. Below is a simplified view of the process:
| Step | Description |
|---|---|
| Encryption at Source | PHI is encrypted as soon as it is created |
| ETL Pipeline Transmission | Data remains encrypted in transit and at rest |
| Storage in Snowflake | Ciphertext is stored, minimizing exposure risk |
| Decryption on Demand | Approved users decrypt only when necessary |
Keeping data encrypted at all times helps thwart insider leaks by limiting the number of opportunities for theft or misuse.
On-Demand Decryption for Authorized Roles
Snowflake’s secure environment further refines this strategy by allowing decryption only when authorized roles need data access. “Only decrypt on-demand for authorized roles” reduces the attack surface, ensuring that sensitive healthcare records are never exposed to unnecessary risk or prying eyes.
HIPAA Compliance and Preventing Insider Leaks
An encryption-first approach is crucial to meeting the criteria spelled out by HIPAA. Beyond external threats, insider leaks pose a real danger to healthcare data. By combining an end-to-end encryption model with strict role-based decryption controls, organizations create a stronger shield around PHI, ensuring that only the right people have access when absolutely necessary.
Enabling Secure ML and GenAI in Snowflake
Despite these robust security measures, the system still “enables secure ML and GenAI workloads using Snowflake ML and Cortex.” This ensures organizations are not forced to choose between stringent data protection and technological advancement. From advanced analytics to next-generation AI applications, the encryption-first model means data scientists and ML teams can harness the power of artificial intelligence while meeting compliance demands.